Biometric Technologies
Introduction
In an increasingly digital world, where personal data and security breaches are prevalent concerns, traditional methods of identity verification have become less reliable. This has paved the way for the rapid growth and adoption of biometric technologies. Biometrics, the measurement, and analysis of unique physical or behavioral characteristics, offer a promising solution for secure and convenient identity verification. From fingerprint recognition to facial scanning and iris detection, biometric technologies are reshaping the way we authenticate and safeguard our personal information.
The Power of Unique Characteristics
Biometric technologies capitalize on the fact that each individual possesses unique physiological and behavioral attributes. These characteristics are nearly impossible to forge or replicate, making biometrics a powerful tool in combating identity theft and fraud. Unlike passwords or access cards, which can be stolen, lost, or forgotten, biometrics are inherently tied to an individual and cannot be easily compromised.
Popular Biometric Modalities
- Fingerprint Recognition: Fingerprint scanning is one of the most widely recognized and adopted biometric technologies. It analyzes the ridges, valleys, and minutiae points of an individual’s fingerprints to create a unique identifier. Fingerprint recognition is commonly used in mobile devices, access control systems, and law enforcement applications.
- Facial Recognition: Facial recognition technology analyzes facial features, such as the distances between the eyes, nose, and mouth, to identify individuals. It has gained traction in various domains, including airport security, surveillance systems, and mobile device unlocking. Facial recognition is continually evolving to enhance accuracy and overcome challenges such as variations in lighting conditions and facial expressions.
- Iris Scanning: Iris recognition involves capturing high-resolution images of the unique patterns in an individual’s irises. The intricate and stable nature of irises makes them an ideal biometric modality for high-security applications. Iris scanning is used in border control, national ID systems, and restricted access environments where utmost accuracy and reliability are crucial.
- Voice Recognition: Voice biometrics employ unique vocal characteristics, including pitch, tone, and speech patterns, to verify an individual’s identity. It finds applications in call center authentication, voice-controlled devices, and speaker identification in forensic investigations. Advancements in deep learning and artificial intelligence have significantly improved the accuracy and reliability of voice recognition systems.
Benefits and Challenges of Biometric Technologies
Biometric technologies offer several advantages over traditional identification methods. They provide stronger security, reduce the risk of identity theft, enhance user convenience, and streamline authentication processes. Biometrics eliminates the need to remember multiple passwords or carry physical identification cards, simplifying daily interactions.
However, challenges exist in the widespread adoption of biometrics. Privacy concerns regarding the collection and storage of biometric data need to be addressed. Data security measures must be implemented to safeguard against unauthorized access or breaches. Additionally, biometric systems should be designed to accommodate diverse populations and consider individuals with disabilities or physical limitations.
Future Directions of Biometric Technologies
The evolution of biometric technologies shows no signs of slowing down. Advancements in machine learning, deep neural networks, and sensor technology are paving the way for more accurate and robust biometric systems. Mobile devices are increasingly integrating multiple biometric modalities for enhanced security, such as combining fingerprint and facial recognition.
Research and development efforts are focused on developing contactless biometrics to meet the demand for hygienic and touchless solutions, especially in a post-pandemic world. Gait analysis, vein recognition, and palm print identification are among the emerging modalities that offer unique characteristics for biometric identification.
Type Of Biometric Technologies
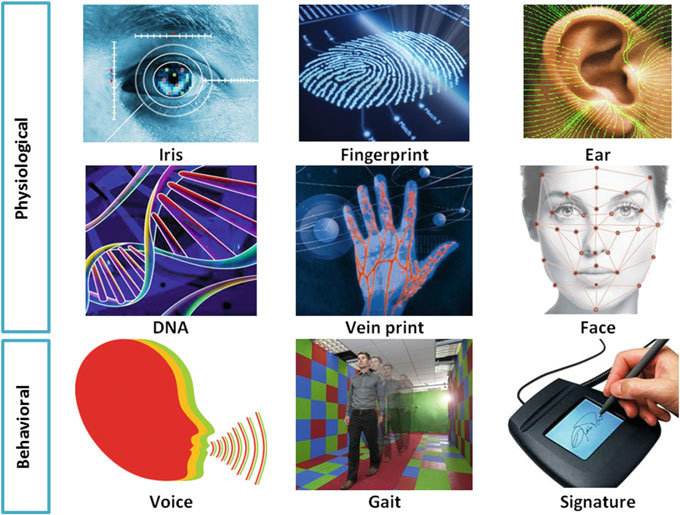
Fingerprint Recognition: Fingerprint recognition involves capturing and analyzing the unique patterns of ridges and valleys on an individual’s fingertips. It is widely used in applications such as access control systems, smartphones, and forensic investigations.
Facial Recognition: Facial recognition technology uses algorithms to analyze and compare facial features, such as the distance between eyes, nose, and mouth, to establish identity. It finds applications in security systems, surveillance, and authentication on mobile devices.
Iris Scanning: Iris scanning technology captures the detailed patterns of the iris, the colored part of the eye, to create a unique identifier. It offers high accuracy and is utilized in national ID programs, airport security, and high-security facilities.
Retina Scanning: Retina scanning involves capturing the unique patterns of blood vessels at the back of the eye. It requires specialized equipment and is primarily used in high-security applications such as government facilities and military installations.
Voice Recognition: Voice recognition technology analyzes vocal characteristics, including pitch, tone, and speech patterns, to verify a person’s identity. It is used in applications such as phone banking, voice assistants, and authentication in call centers.
Hand Geometry: Hand geometry recognition measures the size and shape of an individual’s hand and fingers. It is commonly used in physical access control systems and time and attendance tracking.
Signature Recognition: Signature recognition technology analyzes the dynamic features and patterns of an individual’s signature for verification purposes. It is often used in banking and financial transactions, as well as in legal and forensic settings.
Vein Recognition: Vein recognition technology captures and analyzes the unique patterns of veins in an individual’s hand, palm, or finger. It offers a highly secure form of biometric identification and is utilized in access control systems and healthcare applications.
DNA Biometrics: DNA biometrics use an individual’s genetic information to establish identity. Although still in its early stages of development, it holds potential for forensic investigations and personalized medicine.
Gait Recognition: Gait recognition technology analyzes an individual’s walking pattern, including stride length and speed. It finds applications in surveillance systems and security checkpoints.
Keystroke Dynamics: Keystroke dynamics involve analyzing an individual’s typing rhythm and keystroke patterns for identification. It is commonly used for continuous authentication in computer systems.
Ear Recognition: Ear recognition technology analyzes the unique shape and features of an individual’s ear for identification purposes. It is still in the early stages of development but holds potential in surveillance and security applications.
Each biometric technology has its strengths, limitations, and suitable applications. Depending on the specific requirements and level of security needed, organizations and systems may choose to employ one or multiple biometric modalities to ensure accurate and reliable identity verification.
Uses of Biometric Technologies
Access Control: Biometrics are extensively used for access control systems, replacing traditional methods such as keys, access cards, or PINs. Fingerprint, iris, or facial recognition systems are employed to grant or deny access to secured areas like offices, government buildings, data centers, and residential complexes.
Time and Attendance Tracking: Biometric technologies are used to accurately record employees’ working hours. This eliminates time theft and fraudulent attendance practices. Biometric systems, such as fingerprint or palm scanners, ensure that only authorized individuals can clock in and out, enhancing payroll accuracy.
Identity Verification: Biometrics provide a reliable method for identity verification in various contexts. This includes border control, airport security, and immigration checks, where fingerprint, iris, or facial recognition systems help verify travelers’ identities against their official documents.
Mobile Device Security: Many smartphones and tablets now feature built-in biometric sensors, such as fingerprint or facial recognition, for unlocking the device, authorizing app purchases, and securing sensitive data. Biometrics adds an extra layer of security beyond PINs or passwords.
Financial Transactions: Biometrics are increasingly used for secure financial transactions. Fingerprint or facial recognition can be employed to authenticate users in mobile banking apps, authorize electronic payments, or provide secure access to ATMs.
Law Enforcement and Forensics: Biometric technologies play a vital role in law enforcement and forensics. Fingerprint identification has long been used for criminal investigations, and facial recognition systems help match suspects to surveillance footage. DNA biometrics aid in identifying individuals in forensic cases.
Health and Healthcare: Biometric technologies find applications in the healthcare industry for patient identification, securing electronic health records, and access control in hospitals and clinics. Biometrics can enhance patient safety and prevent medical identity theft.
Border Control and Travel: Biometrics are utilized in border control systems to verify the identities of travelers. This includes fingerprint, iris, or facial recognition for passport control, enhancing security, and streamlining the immigration process.
Smart Homes and Internet of Things (IoT): Biometrics can be integrated into smart home systems to provide secure access to premises, control home automation, and customize settings based on individual preferences. Voice recognition is also used to interact with voice-enabled devices.
Customer Experience and Personalization: Biometrics enable personalized experiences and enhanced customer service. For example, facial recognition can be used to identify loyal customers in retail stores or hotels, providing tailored services and recommendations.
Education: Biometric technologies are employed in educational institutions for student attendance tracking, access control to restricted areas, and securing examination processes to prevent cheating.
Voting Systems: Biometrics offer secure and reliable methods for voter identification and preventing electoral fraud. They can be utilized for voter registration, authentication, and ensuring the integrity of elections.
Advantages of Biometric Technologies
- Enhanced Security: Biometrics provide a higher level of security compared to traditional methods such as passwords, PINs, or access cards. Biometric identifiers, such as fingerprints or iris patterns, are unique to each individual and difficult to forge or replicate. This uniqueness makes it extremely challenging for unauthorized individuals to gain access, reducing the risk of identity theft and fraud.
- Convenience and User Experience: Biometric technologies offer a convenient and seamless user experience. Users no longer need to remember multiple passwords or carry physical identification cards. With biometrics, the authentication process becomes faster, easier, and more user-friendly. Users can simply scan their fingerprints, look at a camera, or speak into a microphone to verify their identity.
- Non-Transferable and Non-Lossable: Biometric identifiers are inherently tied to an individual and cannot be easily transferred or lost. Unlike passwords or access cards that can be shared or stolen, biometric characteristics are unique to each person and cannot be separated from them. This adds an extra layer of security, ensuring that only the authorized individual can access their personal information or restricted areas.
- Improved Accuracy and Reliability: Biometric systems have significantly improved in accuracy and reliability over the years. Advancements in technology, such as high-resolution sensors and advanced algorithms, have made biometric recognition more precise and robust. This reduces the chances of false positives or false negatives, providing more accurate identification and verification results.
- Audit Trail and Accountability: Biometric technologies can create an audit trail, providing a record of who accessed a particular area or performed a specific action. This feature enhances accountability and can be valuable for forensic investigations or regulatory compliance purposes.
- Scalability and Integration: Biometric systems can be easily scaled to accommodate large user populations. They can be seamlessly integrated with existing security infrastructure, such as access control systems, time and attendance tracking, or mobile devices. Biometric technologies are flexible and can be customized to fit specific business needs and security requirements.
- Hygiene and Touchless Solutions: With the increased focus on hygiene and touchless interactions, biometric technologies offer an advantage. Contactless biometric modalities, such as facial recognition or iris scanning, eliminate the need for physical contact, reducing the risk of spreading germs or viruses.
Disadvantages of Biometric Technologies
- Privacy Concerns: Biometric data, such as fingerprints or facial features, is highly personal and sensitive. There are concerns about the collection, storage, and potential misuse of this data. If biometric databases are breached or compromised, it can result in identity theft or unauthorized access to individuals’ biometric information.
- Inherent Biometric Characteristics: Biometric identifiers, such as fingerprints or iris patterns, are considered to be unique to each individual. However, there can be instances of false positives or false negatives in biometric recognition systems. Factors like variations in biometric traits due to injury, aging, or changes in appearance can sometimes result in incorrect identification or verification.
- Cost and Implementation: Implementing biometric systems can be costly, particularly for organizations with large user populations. The initial investment includes acquiring the necessary hardware and software, integrating them into existing infrastructure, and training personnel. Additionally, maintaining and updating biometric systems also requires ongoing investments.
- Cultural and Social Acceptance: Biometric technologies may face cultural or social resistance in some regions or communities. Concerns regarding privacy, personal beliefs, or cultural norms may influence individuals’ acceptance and adoption of biometric systems.
- Vulnerability to Spoofing or Attacks: Biometric systems can be vulnerable to spoofing or attacks, where malicious individuals attempt to deceive the system by presenting fake biometric traits. For example, fingerprint or facial recognition systems can be tricked using high-resolution images or 3D printed replicas of biometric features. Continuous advancements in technology are required to address such vulnerabilities.
- Lack of Standardization: The lack of standardized biometric systems and formats can pose challenges in interoperability and compatibility. Different systems may use varying algorithms, data formats, or biometric modalities, making it difficult to integrate or share biometric data across different platforms or organizations.
- Ethical and Legal Considerations: The use of biometric technologies raises ethical and legal considerations, including issues related to consent, data protection, and discrimination. Ensuring proper consent, transparent data practices, and compliance with privacy regulations are essential to mitigate these concerns.
Examples of Biometric Technologies
Imagine Sarah, a smartphone user who relies on biometric technology for securing her device. She owns a smartphone equipped with a fingerprint sensor and facial recognition capabilities.
When Sarah wants to unlock her phone, she simply places her registered finger on the fingerprint sensor located on the device’s home button. The sensor captures a detailed image of her fingerprint and compares it to the stored fingerprint template in the device’s secure memory. If the captured fingerprint matches the template, the phone unlocks, granting Sarah access to her personal information, apps, and data.
In another scenario, Sarah’s phone is placed on a table, and she wants to unlock it without touching it. She looks at the phone’s front-facing camera, which is equipped with facial recognition technology. The camera captures an image of her face, analyzes the unique facial features, and compares them to the registered facial template stored on the device. If the facial recognition algorithm confirms a match, the phone unlocks, providing Sarah with seamless and secure access to her device.
These biometric security features offer several advantages to Sarah
- Enhanced Security: The biometric technologies employed by Sarah’s phone provide a high level of security. Fingerprint recognition and facial recognition are difficult to replicate, making it challenging for unauthorized individuals to gain access to her device.
- Convenience: Sarah no longer needs to remember complex passwords or patterns to unlock her phone. The biometric sensors offer a quick and convenient way to authenticate her identity and access her device.
- Personalization: Biometric technologies allow for a personalized user experience. Sarah’s phone recognizes her unique biometric traits, customizing settings, preferences, and even app recommendations based on her individual profile.
- Secure Mobile Payments: Sarah can utilize biometric authentication for mobile payment services. When making purchases, she can verify her identity using her fingerprint or facial recognition, adding an extra layer of security to financial transactions.
- Data Protection: Biometric security helps protect Sarah’s personal data, such as messages, photos, and sensitive information stored on her device. Unauthorized access is significantly mitigated, ensuring her privacy.
Conclusion
Biometric technologies have emerged as a game-changer in identity verification and security. By harnessing the power of unique physical and behavioral characteristics, these technologies provide a reliable and convenient means of authentication. As biometrics continue to advance, they hold the potential to revolutionize not only personal security but also transform various.



Supub article information.
Thanks
[…] Read Also…Biometric Technologies […]
[…] Read Also..Biometric Technologies […]